Online scanners can be useful tools to identify malicious files or URLs. However, some common user behaviour can lead to unintentional data leaks. This article will give a quick overview of how this can happen, and what you can do to prevent it.
What causes data leaks?
Every online scan tool requires users to upload information, usually files or URLs, in order to work. This immediately creates a situation where information leaves the confines of your organisation. Furthermore, many platforms actually share this data with some of their users for research purposes.
As stated by Virustotal, the largest online scanner to date, « The contents of submitted files or pages may also be shared with premium VirusTotal customers. The file corpus created in VirusTotal provides cybersecurity professionals and security product developers valuable insights into the behaviours of emerging cyber threats and malware. Through our premium services commercial offering, VirusTotal provides qualified customers and anti-virus partners with tools to perform complex criteria-based searches to identify and access harmful files samples for further study. This helps organisations discover and analyse new threats and fashion new mitigations and defences. »
If users in your organisation upload sensitive files, the entire contents of these files could therefore be available to unknown third parties.
URLs may also contain some potentially sensitive information. This is usually underestimated since the information is generally publicly available on the internet. However, through some tools, it can accidentally reveal things about your users' browsing habits.
One such case that was recently reported to us concerns the Belnet Advanced Mail Security (BAMS). A feature of this product is that it checks links in e-mails and makes the end-user go through BAMS before reaching a potentially dangerous site. A side effect of this feature is that the end-user may encounter links which are prepended with the « [organisation name].bams.belnet.be » domains.
If users start regularly checking such URLs, it creates a set of data which can be searched and analysed. Urlscan.io, for example, offers this feature to anyone :
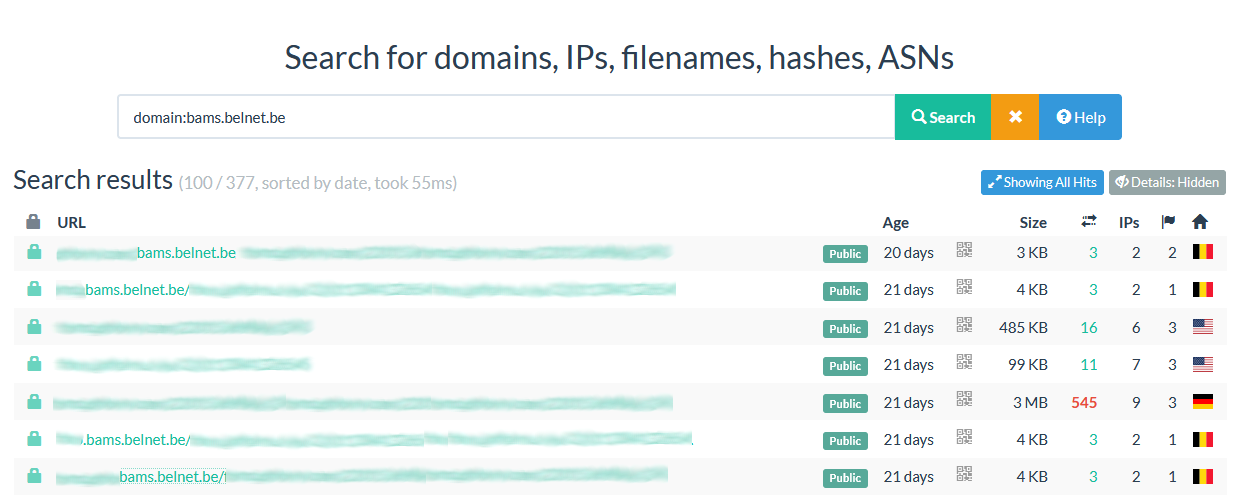
Third parties may therefore be able to gather insight into what sites your users browse. They could even send test phishing mails and check whether or not your users are sending those links to public scanners.
What can you do about it ?
As an organisation, it is important to spread awareness to make sure your users understand the risks involved with using online scanners. Ideally you should inform them about who they can contact internally regarding suspicious files or links to reduce the dependency on external tools.
Training on the various security tools you use is also useful. For example the anti-virus solution you provide may allow users to scan files locally on demand, and familiarising them with tools such as Belnet Advanced Mail Security may stop them from considering the modified URLs as suspicious. Finally, you may also train your users in ways to use online scanners responsibly, as we will cover next.
Good practices
For users, there are some behaviours you can adopt to eliminate or reduce the risks of using external scanners.
The most important thing is to never upload files that might contain sensitive information. For example, if you receive a suspicious file from HR/Accounting/a project manager..., you should probably not upload it and instead confirm through different means (e.g. by phone or in-person) whether or not the mail is legitimate.
If you choose to proceed with the scanner, there are some options you can use to make this safer. For example, urlscan.io which we discussed earlier lets you choose the visibility level of your search, i.e. who can see the URLs that you checked. The default is public, but you can set it to private with a few clicks :

For files, most tools will allow you to search on file hashes instead. In this case, instead of uploading the file itself, you check whether or not the file was already uploaded by someone else by using the hash as a « unique » identifier for it. The results are not as complete since this requires someone else to have received the same file, but it can help detect a phishing campaign while eliminating the risk of accidentally leaking data.
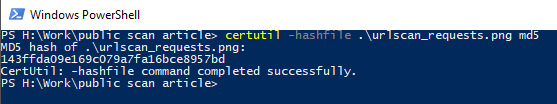
The hash of a file can be obtained in several ways, for example on Windows by using the command 'certutil -hashfile [file name] MD5' in Powershell or cmd.
Linux users can use 'md5sum [file name]' The 32 character output can then be copy-pasted into the search bar of the online tool.
About the author
Benjamin Baugnies studied civil engineering in Louvain-la-Neuve and has been working as a security analyst at Belnet for 6 years. In addition to day-to-day security operations, he has worked on projects such as vulnerability scanning, netflow monitoring, and DDoS protection. Outside of work, he can often be found on a tennis court, in the kitchen, or on some on-line game.