By now everyone knows that a strong and secure password is a must when using anything IT related. But what makes a password strong and how do we store these passwords in a secure way?
How does a password get cracked?
There are several ways to hack a password, with the easiest being is simply buying a password from the dark web. But there are many more ways to hack a password.
The most known way is to bruteforce a password. This means that an attacker tries to guess with every combination in the book until it hits your password. This is done with a piece of software that tries as many combination in the shortest time. Generally anything under 12 characters is vulnerable to being cracked.
Another way of hacking a password is by using a dictionary attack. This attack does exactly what it sounds like. An attacker will attack you with a predefined list of “passwords”. As with a bruteforce attack a piece of software will try all those passwords until it guesses the right one. If your password is a regular word it will only survive a dictionary attack if the word is very uncommon.
The most abhorrent way of an attacker obtaining a password is through phishing. This is when an attacker tries to trick, intimidate or pressure a user into unwittingly doing what the attacker wants. Phishing cannot only come in the way of emails but also through text messages (smishing) and through phone calls (vishing).

How to create strong passwords?
Now that we know how passwords are cracked, we can create strong passwords that outsmart each attack (except phishing, outsmarting phishing just means to not fall for it).
Raf Gillisjans: "you should make your password long, this might even be the most critical factor in securing yourself from a bruteforce attack."
- Firstly you should make sure that every password you use is unique. Reusing passwords makes it easy for criminals to get access to multiple accounts if they find out just one of your passwords, especially your email.
- Don’t use any sequential numbers or letters (‘abcdefg’,’123456789’). You should also never use memorable keyboard paths. As with advice above about sequential letters and numbers, do not use sequential keyboard paths either.
- Make sure it also doesn’t contain any personal info such as your name or date of birth. If you’re being specifically targeted, the attacker will put every piece of info they know about you in their guessing attempts. Remember it can be surprisingly easy for them to find out basic personal information about you. So, be careful how much information you give away on social media.
- To circumvent a brute force attack you can take a couple of specific steps. Firstly you should make your password long, this might even be the most critical factor in securing yourself from a bruteforce attack. Anything up from 15 characters is almost unbruteforceable (it would be way too long).
- Further you should use a mix of characters, the more you mix up letters, numbers, punctuation marks and symbols, the harder to bruteforce a password.
- Lastly, avoid common substitutions, password crackers mostly know the usual substitutions. Whether you use HELLO or H37L0, the brute force attacker will crack this with equal ease. The biggest method to stave off a dictionary attack is by ensuring the password isn’t just a single word. Multiple words will confuse this tactic (like a passphrase. Choose one that is only meaningful to you, so no familiar phrases or proverbs).
Password managers
In today's digital world, there are ever more passwords that you have to remember: your e-mail account, your social media accounts, applications you use for study or work, applications for online banking, web shops, ... We all have dozens of passwords to remember.
Raf Gillisjans: "A password manager is also an excellent solution for keeping the passwords of accounts you share with your fellow colleague or students"
As stated above it is recommended to use a unique password for every login you have. Keeping track of those can get quite hard, therefore it is most important to use a password manager. This is a tool that lets you store and generate strong passwords. And so, instead of needing to memorize all your login credentials, you just have to remember one master password that unlocks your password manager.
A password manager is also an excellent solution for keeping the passwords of accounts you share with your fellow colleague or students. For example, a tool you use to work together on a project.
There are 3 types of password managers:
- Locally installed/offline password managers
- Web-based/online password managers
- Stateless/token-based password managers
A locally installed password manager, as the name suggests, is a password manager which stores your data on your own device, locally. If you keep this device offline it eliminates the risk of someone breaching your password vault but you can only access your vault on only one device and if you lose that device all your data is lost.
Web based password managers store your passwords in the cloud, which is usually the providers server. This means you can access your passwords from anywhere as long as you have an internet connection. Reputable service providers use a zero-knowledge technology. That means that they encrypt the data on your device before sending it over to the server. But it also means that your vault is available for access attempts 24/7.
Stateless password managers are a local piece of hardware, such as a USB device that contains a key to unlock your particular account. There is no such thing as a password vault when using a token-based password manager because it generates a new token everytime you want to log in. But as with offline password managers, if you lose the device, you lose your access.
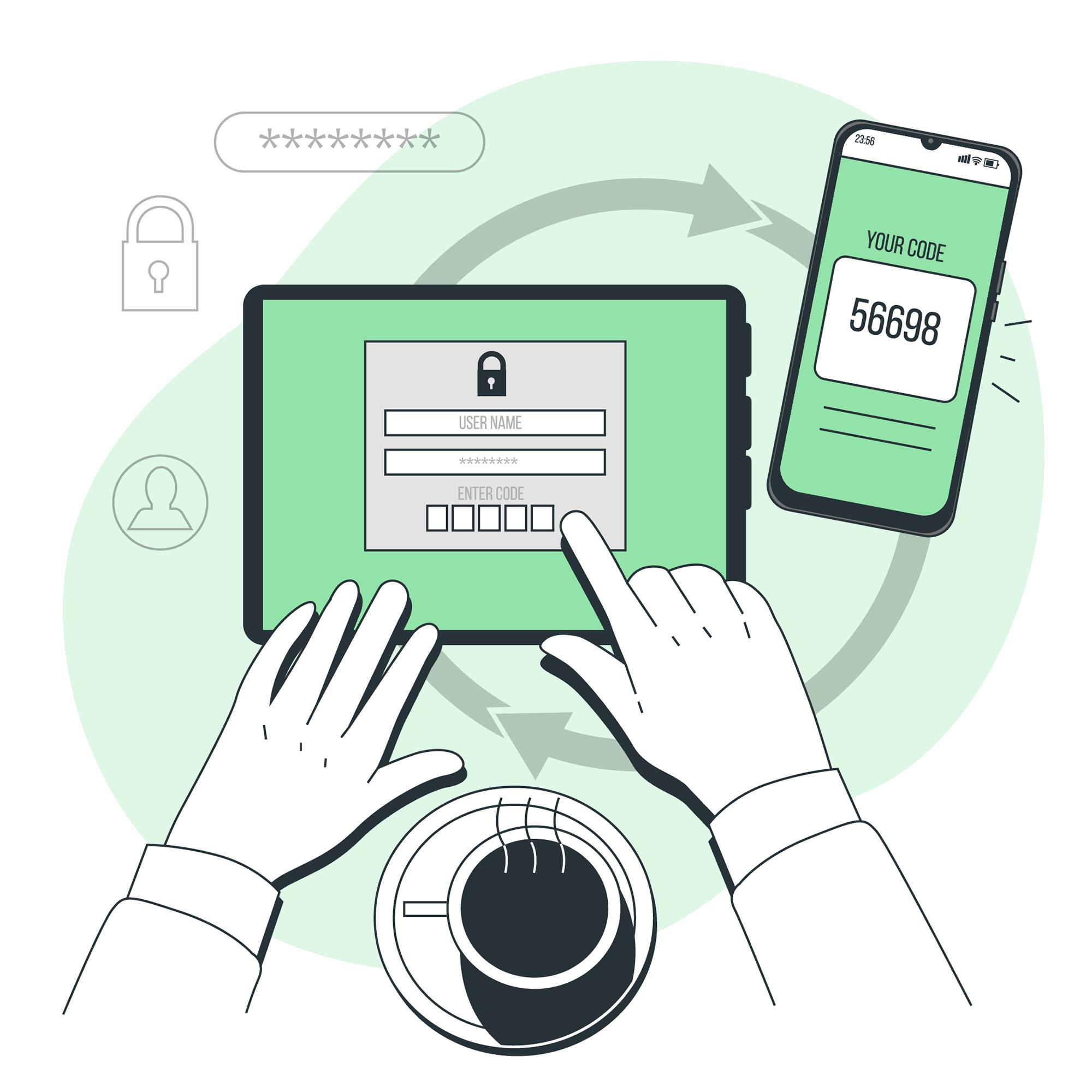
Multi-Factor Authentication (MFA)
To make your accounts even harder to break into, enable MFA. This means your account ‘double checks’ if it’s you trying to login. Or someone pretending to be you. The principle is simple: two-factor authentication uses something you know (your password) in combination with something you have or are (e.g. a fingerprint).
There are various forms of multi-factor authentication, one of the most commonly used is an access code sent to one of your trusted devices. You then use this code to complete the login process. Hackers will not be able to access your account from your username and password alone.
There are also other methods of MFA, such as using Google Authenticator App or physical keys.
Many Internet services and social media offer multi-factor authentication: you can set it up on WhatsApp, Apple, Google, LinkedIn, Twitter, etc., among others.
What if my password has been hacked?
It may happen that a website or online service you are using has been hacked. As a result, your login details can be found on the internet. You may also have clicked on a fake email and shared your password with cybercriminals without realising it.
If you still have access to your account, you must change your password immediately. If you no longer have access to your account, you need to restore your account and then change all your passwords.
Notify your bank immediately if the attackers have gained access to your bank details! If your professional e-mail or applications related to your studies or work have been hacked, alert your organisation's IT department.
Have I been pwned ? (https://haveibeenpwned.com/)
HIBP or "Have I Been Pwned?" is a website that allows internet users to check whether their personal data (passwords) has been compromised. This website collects and analyzes data dumps and pastes containing information about leaked accounts, and allows users to search for their own information by entering their username/email address. The website in its turn then shows in what breaches this email address or username appears. As user you can also sign up to be notified if your email address shows up in future dumps.
Raf Gillisjans: "Have I been pwned collects and analyzes data dumps and pastes containing information about leaked accounts"
When you run a query for your credentials and it shows up you’ve been breached it is recommended to change your password on this website and every other website where you used the same password.
About the author
Raf Gillisjans studied applied computer science in Bruges and has been a part of the security team at Belnet for almost 2 years. He evaluates new solutions to make the Belnet environment a more secure place and is also part of the security awareness team. Outside of Belnet he can be found in a radio studio, behind a camera or behind his pc playing some game.